A scope is a role that defines access to various information or code sections. There are two kinds scopes and in Identity Server they are defined as :
- Identity Scopes
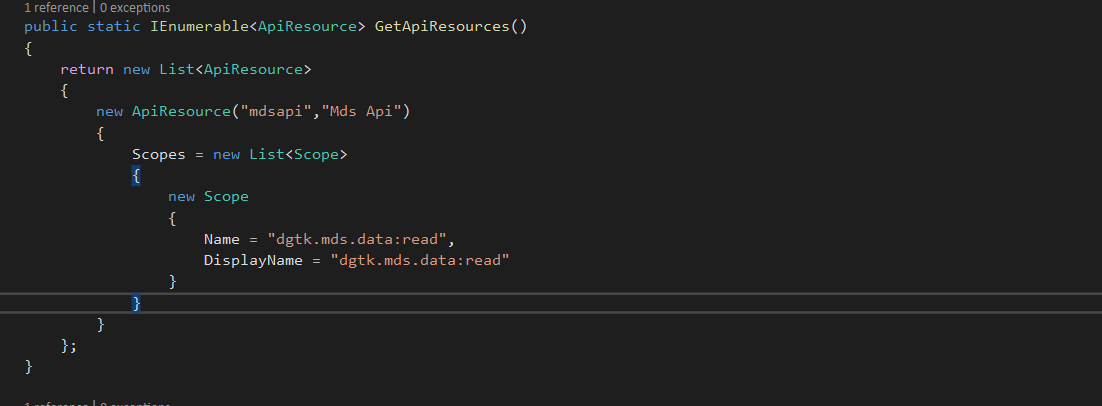
- Api Resource Scopes
Scopes define the access information target for which that the client can request. When requesting an identity resource scope then you will demand for identity information. When requesting an api resource scope then you will demand for access to an api.
1. Custom Identity Resource
In identity server there are several built-in identity resources, but you can also define your own resource.
a. Definition
An identity resource has meaning as long as it has a claim. Therefore there is a requirement that an identity resource must have minimum 1 claim in the claims list. In the example below we define an identityresource with the scope name customIdentityScope having a custom claim called my_pet_name.
For this scope to be available to an authorization request, we must also included in the client’s definition.
We can now use this to populate our claim’s content for our user :
b. Using the flow in the client with the IdentityModel package
This is an authorization flow, so to use this we need to first make a redirect containing the scope we want the authorization code for, and when we receive this code we should from the backchannel demand the authorization token for this:
We can now see that when making a user introspection request using an access token we will receive our custom claim
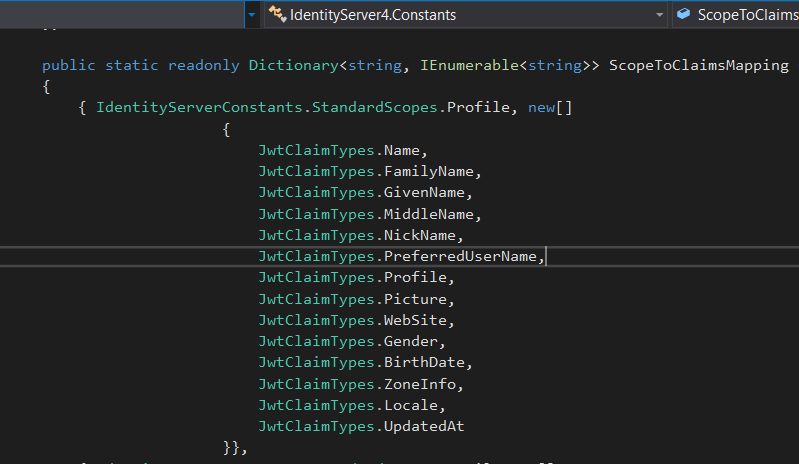
2. Built-In Identity Resources
There are several identity resources built in the IdentityServer framework. To identity what scopes and clames they map to, we have to look a bit under the hood.
a. StandardScopes
Under IdentityServerConstants.cs we can see the following constants defined: